
SYSCIP® OVERVIEW
SysCIP®, (SysNet Technologies Critical Infrastructure Protection) methodology is comprehensive and unique in the federal Information System Security (ISS) services industry. Our methodology was formalized by SysNet Technologies (SysNet) in late 1999 and is regularly updated and evolves to incorporate all new and changing applicable federal, agency, and industry regulations, standards, and processes for cybersecurity. The regular SysCIP® updating facilitates staff training and procedural currency. The currency and over 20-year history of consistent successful usage ultimately result in highly effective information systems security for federal agencies.
SysNet utilizes SysCIP® for continuous and consistent state-of-the-art ISS services. As evidence of the SysCIP® effectiveness, this methodology has enabled continuous success for the Federal Aviation Administration (FAA) Air Traffic Organization National Airspace Systems from the beginning of SysNet’s FAA ISS support. As done for the FAA, SysNet staff including all team member personnel, utilize the most effective tools for all program areas ranging from Risk Management Framework support to Cloud Systems support.
SysCIP® service areas are modular and therefore one of the inherent values that SysNet brings to federal agencies is orientation and training of all new personnel and personnel supporting new areas, for consistent agency systems protection. As agency systems are added or changed, SysCIP® is utilized to ensure our employee and overall team comprehensive protective services. SysCIP® will enable the complete application of technical skills, and documentation and reporting. SysNet teams with companies for the agency-specific knowledge and relevant expertise, to maximize the agency ISS. SysCIP® modules include the following:
| 1. Information Assurance & System Security Audits 2. Risk Assessments and Vulnerability Analyses A&A (Assessment and Authorization) methodology System Security Plan (SSP); Tiers, Requirements, Core Controls SAR (Security Assessment Report) POA&Ms (Plan of Action & Milestones) 3. Enterprise Compliance and Continuous Monitoring 4. Cyber Threat Hunting 5. Application, System and Network Penetration 6. Red Team & Cyber Offense / Blue Team & Cyber Defense 7. Security Testing Standard Operating Procedures 8. ISCP (Information System Contingency Plan) 9. Security Requirements, Tailoring, and Training 10. ISCM (Information Security Continuous Monitoring) | Security Posture Monitoring & Assessments System Baseline Configuration Change Monitoring Authorization Status Reporting, Document Updates, and Management Remediation Management Security Posture Monitoring and assessments System Baseline Configuration Change Monitoring System Ongoing Authorization and FISMA Reporting Incident Response and Resolution |
Following are some examples of SysCIP® modules.
A&A (Assessment and Authorization) Methodology
SysCIP® goes beyond basic RMF (Risk Management Framework) implementation steps to deliver the technical and administrative service an agency needs to excel for Low, Moderate and High risk systems. We not only provide the essential technical implementation skills necessary to implement the controls based on the agency’s environment, but our proven SysCIP® documentation templates, process implementation checklists, and continuous monitoring tools provide the initiative the agency will need to complete each RMF step quickly and efficiently. SysCIP® provides a standard process model, supported by full integration of tools and data, to minimize individual variance in approach (seeking consistent results) and minimal human labor. Through the implementation of SysCIP®, SysNet provides the agency an automated, structured, and flexible approach for managing risk.
RMF Steps
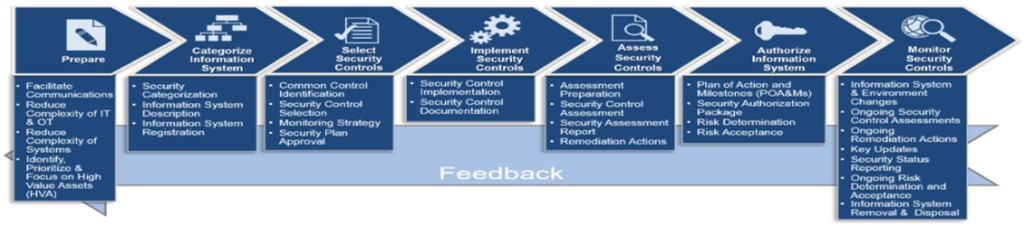
ISCM (Information Security Continuous Monitoring) Implementation Concept
The SysCIP® ISCM functional approach is tailored to agency systems and is based on NIST (National Institute of Standards & Technology) SP 800-37 as illustrated below. The implementation of each major ISCM function and how the agency should evolve the ISCM program and identify roles and responsibilities for its implementation are provided and regularly reported.
SysCIP®, will enable the complete application of technical skills, and documentation and reporting. SysNet teams with companies for the agency-specific knowledge and relevant expertise, to maximize agency ISS, as shown in the below ISCM Functional Overview
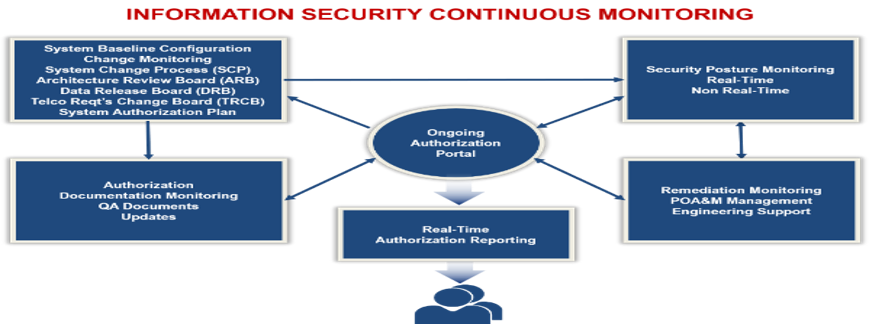
Enterprise Compliance and Continuous Monitoring
Continuous monitoring of agency networks, systems, and data involves an ongoing awareness of information security, vulnerabilities, and threats to facilitate risk-based decision making. Continuous monitoring involves the ongoing assessment and analysis of the effectiveness of all security controls and provides ongoing reporting on the security posture of information systems to support risk management decisions to help maintain risk tolerance. Policy monitoring and documentation updates and significant changes for re-certifications are included.
Continuous monitoring of agency systems is conducted in compliance with three essential requirements:
- Change and configuration management of assets
- Security control monitoring using automated tools
- Documentation updates and reporting
SysCIP® is utilized for 24×7 continuous data monitoring including trouble ticket generation, reporting, and resolution, for example as is done for the FAA NCO (National Airspace System Cybersecurity Operations) command center.
Risk Mitigation & Support
SysCIP® will help determine the specific implementation details according to the technology choices of the agency such as the agency technology road map, available resources, and other factors. SysNet’s unique Risk Translation methodology helps agencies assess risk on both a system and enterprise level.
Lessons Learned Usage
The methodology feedback will provide a clear and concise, prioritized action plan for the agency Chief Information Officer (CIO). In addition to the above, technical security advice is provided. This includes upgrades that can be made to individual components of the agency’s perimeter defenses, and improvements to data storage and encryption policies through long-term wide-ranging recommendations regarding staff and senior management education programs.
Each of the key stakeholders in the agency, such as human resources for education, IT for network infrastructure, Operations for data ownership, and Executive Management for regulatory compliance will usually follow-up and implement the remedial actions recommended by SysNet. SysNet will facilitate the CIO, CISO (Chief Information Security Officer), or the system owner’s construction and delivery of the action plan. This includes the security of the agency’s information policy spanning the executive and senior management teams, for policy effectiveness and staff understanding of the existing threats and defensive actions that all must take to keep the agency secure.
Industry Recognition:The SysCIP© Library of Congress copyright validates the uniqueness of this successful methodology. SysCIP® also is a registered name approved by the U.S. Patent and Trademark Office in recognition of our unique methodology. This has always been a SysNet hallmark methodology from the beginning, for over 20 years. The methodology copyright and name trademark registration are a credit to the strength of our methodology.
SysCIP® is a registered trademark of SysNet Technologies, Inc. – All Rights Reserved.
